We have been working on shoring up our servers for a specific client. Their latest scan showed an issue with CVE-2000-0649 “Web Server Internal IP Address/Internal Network Name Disclosure Vulnerability”
We looked and looked and there is not documentation to fix the issue.
We could replicated it using https://www.exploit-db.com/exploits/20096/
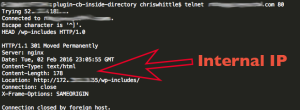
After days of trying to figure it out we finally found a fix.
http://nginx.org/en/docs/http/ngx_http_core_module.html#server_name_in_redirect
server_name_in_redirect
on
Once it’s added to nginx.conf and nginx is reloaded this is what you will see
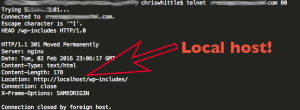
Wait what about my domain? Shouldn’t it be that instead of localhost?
I think it’s because the vulnerability is from HTTP 1.0 which won’t contain the “Host” part of the header.
But I’m not 100% sure…
Maybe I’ll look into it more later but for now it fixes our issue and we can move on.
I hope this helps anyone looking to fix the problem and feel free to comment below if you have a better way or can see any issues with enabling this flag.
Whitt