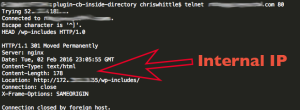
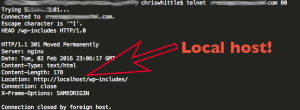
I have been looking for a good responsive table set up for a project I was working on. I ran across a codepen at https://codepen.io/nhackley/pen/QbGoLN and it was exactly what I was looking for (minus a few tweaks and adding the ability to have grouped results)
I cleaned it up and added a Grouped version.
Interested? Go check it out at https://github.com/cwhittl/responsive-react-tables